When you buy any BT broadband or mobile package, you'll get access to over 5 million hotspots dotted around the UK (we've got the largest mobile wi-fi network in the country). And best of all, you'll receive FREE unlimited access. Getting started. Simply use your BT ID to login, using the BT Wi-fi app.
Below are some dictionaries that can be used with Backtrack or Kali Linux. They are plain Wordlist dictionaries used to brute force WPA/WPA2 data captures with aircrack-ng.
These are dictionaries that have been floating around for some time now and are here for you to practice with. Once you get good at using a dictionary,and if these don’t crack the password for you, it would be a good idea to make your own with Crunch.
I have also included Wordlist that come pre-installed with Backtrack and Kali called darkc0de.lst and rockyou.txt
Due to bandwidth and storage limitations I am using free file sharing services Mediafire, Openload, and 4shared to store the files for download.
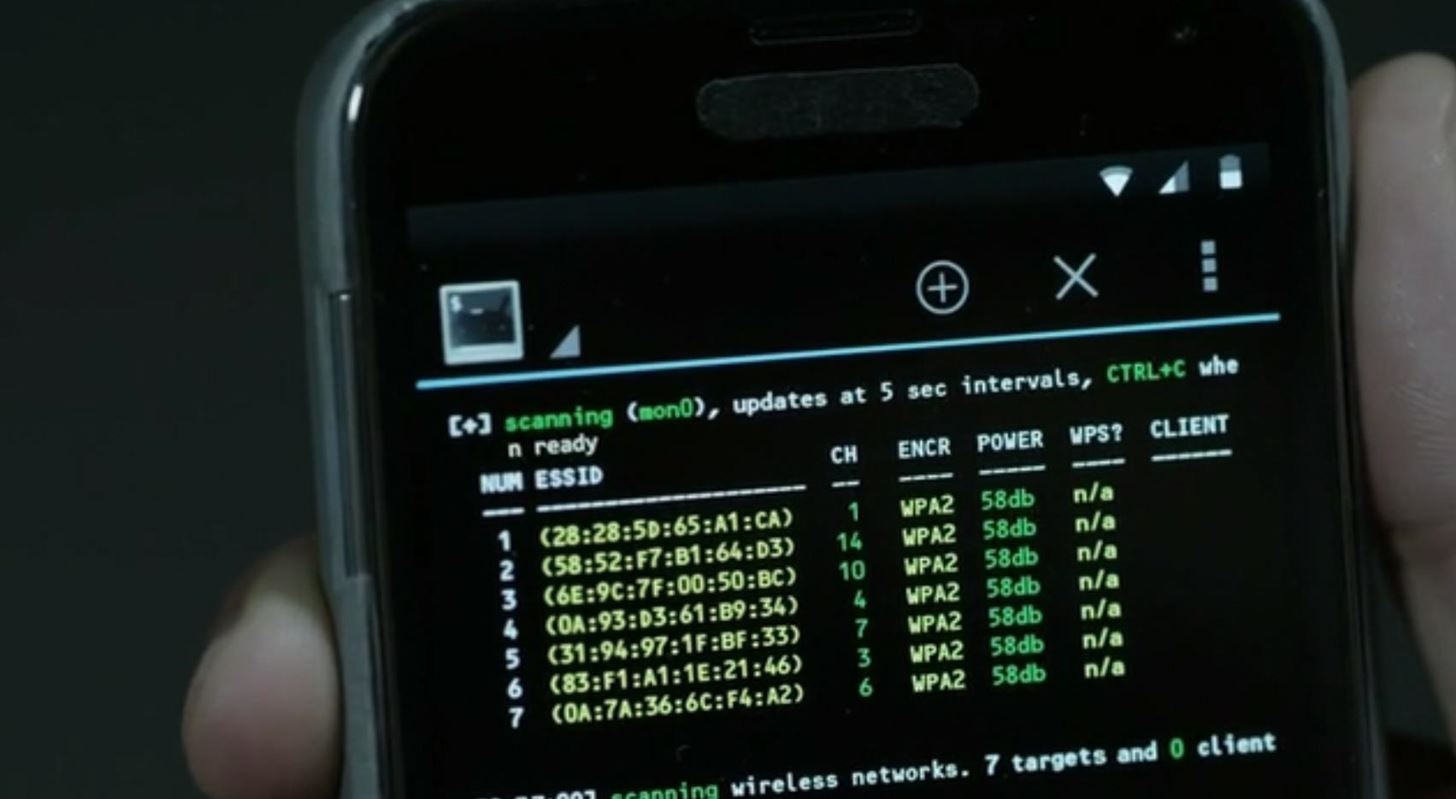
Wireless Pen testing requires an adapter that can go into monitor mode.
WPA/WPA 2 Dictionaries Downloads
If the Wordlist below are removed here is a Torrent link to download a 8.5GB collection of WPA/WPA2 Wordlist Dictionaries. A Torrent client will be needed.
The Big WPA List files will need to be extracted after downloading.
Direct Download Links
BIG-WPA-LIST-1 MediaFire 247MB
BIG-WPA-LIST-1 Openload 247MB
BIG-WPA-LIST-1 4shared
BIG-WPA-LIST-2 MediaFire 307MB
BIG-WPA-LIST-2 Openload 307MB
BIG-WPA-LIST-2 4shared
BIG-WPA-LIST-3 MediaFire 277MB
BIG-WPA-LIST-3 Openload 277MB
BIG-WPA-LIST-3 4shared
Darkc0de.lst MediaFire 17.4MB Default Backtrack 5 Dictionary
Darkc0de.lst Openload 17.4MB Default Backtrack 5 Dictionary
Rockyou.txt133MB Default Kali Linux Dictionary
Rockyou.txt Openload 133MB Default Kali Linux Dictionary
Names MediaFire 3.7MB Long file list of names and name variations
Names Openload 3.7MB Long file list of names and name variations
So i was adding a wireless device to my BThub4 and typing in the password i realised that no characters were after f so immediately thinking this hex must be generated someways i delved online and found some material on gnucitizen on a researcher who cracked the generation for the old the old BTHub 1.0 based on the Thomson SpeedTouch 7G and ST790. Although this was WEP encryption to give an idea of how dated this is.
information on some of the hubs here
https://en.wikipedia.org/wiki/BT_Home_Hub
I experimented with sha-1 hashing the serial number of the newer routers and found the method (as expected) no longer works, However using an old bthub 2 and bt hub 4 I see that:
- The SSID format still remains the same i.e BTHub4-XXXX where x can be 0-9 or A-Z all uppercase (on the hub stickers)
- Serial number format is the same i.e. +XXXXXX+AAAAAAAAAA where X is 0-9 and A is A-Z case insensitive things i noted are that the first X was 0 across the 3 hubs i tried are all 0 though this may herald nothing special, and on the two BTHub 4 models the first 3 A characters were NQ3 (note these two were acquired in a small timeframe from BT which may explain this )
- wireless keys are a strict length 10 and in a hex range so 0-9 a-f case insensitive of course - here is an intriguing part where i will really require other home hub users to assist, there is some simple recurrence i've noticed in the wireless passwords that i hope other users can confirm, the characters c 6 d appear in all models tested with things like db pairs appearing and the number 9 frequenting in the keys hopefully this may make it easier to determine how the key is generated eg SHA-1 hash etc.. or it may be completely trivial I am really out on a longshot here. I will post full info on two of the hubs the other i cannot as i am not the owner and it is still active
- the admin password is 8 long and can be 0-9 or A-Z upper case (login manager is case sensitive)
So as we can see there is set rules for these fields persisting across the hub versions (there is currently 5) but something changed from the original to how this is done but what? was some salt added to the hash? another hashing method used?
If interest is shown in this topic i will post details on my BTHub 3 as well and will see if i can acquire more complete hub info using the helpful google and ebay pictures of hubs for sale and would encourage readers to post any they may know (preferably old ones as well its all the information you need to own the router)
SSID - BTHub2-QR5H
SERIAL NUMBER - +044024+1105986137
MAC - C0D044BEDDC8
WIRELESS KEY (WPA) - 5dbca439c6
ADMIN PASSWORD - Y6FFYN34
WIRELESS PIN - 2695-0761
SSID - BTHub4-29ZR
SERIAL NUMBER - +068341+NQ31245897 (maybe only first two characters are letters?)
MAC - 2C399662E812
WIRELESS KEY (WPA & WPA2) - cfa6d494a8
ADMIN PASSWORD - XMJHT3MJ
WIRELESS PIN - not printed on the hub & haven't successfully hacked with reaver to find.. yet
- cover image is another hub too for bonus info ;P
Wifi Login Xfinity
I hope to hear from you all soon i hope i have provided adequate information for any cracker out there to take a shot at this and if you need more information don't hesitate to comment or message and hope you enjoy a different perspective on WiFi/Router hacking